On the same topic...
Discover links to related pages to deepen your knowledge and explore similar topics.
Disclaimer: The ‘questions and answers’ section below is intended to improve the understanding of the provisions of the NIS 2 Directive by those concerned. However, it does not constitute a final interpretation of the various terms of the NIS 2 Directive and the general explanations provided by the Institute may vary over time and in particular depending on the transposition of the NIS 2 Directive into Luxembourg law.
Directive (EU) 2016/1148 of the European Parliament and of the Council of 6 July 2016 concerning measures for a high common level of security of network and information systems across the Union (hereinafter referred to as the ‘NIS1 Directive’) was drawn up with the aim of contributing to the secure functioning of the economy and society in the European Union (hereinafter referred to as the ‘EU’). In this context, the objectives were in particular:
Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on measures for a high common level of cybersecurity across the Union, amending Regulation (EU) No 910/2014 and Directive (EU) 2018/1972, and repealing Directive (EU) 2016/1148 (NIS 2 Directive) (hereinafter, the ‘NIS 2 Directive’) seeks to make necessary improvements to NIS 1 in the face of the changing cyberthreat landscape and aims to limit the divergences in the transposition of NIS 1 identified by the various Member States. Overall, the new features of NIS 2 are as follows:
According to Article 41(1) of the NIS 2 Directive, Member States must adopt and publish the provisions necessary to comply with the NIS 2 Directive by 17 October 2024 at the latest. They must apply them from 18 October 2024. These dates relate to the adoption of a law transposing the NIS 2 Directive (hereinafter the ‘NIS 2 Law’) at national level.
After the entry into force of the NIS 2 Law, the ILR will have to update or, if necessary, prepare its regulations for the sectors for which the ILR will be the competent authority. The entities will be informed and consulted on this matter. The regulations will define at least the procedures relating to security measures and incident notifications and the various deadlines to be met by the entities.
At the same time, the ILR is working on guidelines to support the entities in the application of the measures to help them comply with the regulations.
However, the ILR strongly advises entities to already proceed with the preparation and implementation of security measures in accordance with European and international standards and to closely monitor the transposition of the NIS 2 Directive in the Grand Duchy of Luxembourg.
To help you determine whether your company falls within the scope of the NIS 2 Directive, please refer to the simplified diagram below.
As indicated in this diagram, the NIS 2 Directive introduces a rule for determining the scope of application linked to the size of the company, also known as the ‘size-cap’. This means that a company that is active in one of the sectors of the annexes and if this company is of a certain size (see below the section ‘Explanations on the size-cap’) is by default concerned by the NIS 2 Directive.
In addition, the NIS 2 Directive provides for several exceptions to the application of the ‘size-cap’ (for example: for providers of public electronic communications networks or publicly available electronic communications services, for trust service providers or top-level domain name registries and domain name system service providers).
Regardless of its size, an entity may be identified as essential or important according to specific criteria (for example: entity already identified as a critical entity; sole supplier in its field of activity, etc.).
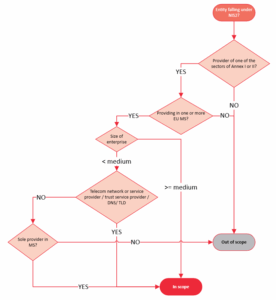
For more information, please consult our page on the scope and field of application of the NIS2.
The diagram below provides an overview of the process for determining whether an entity is to be considered essential or important.

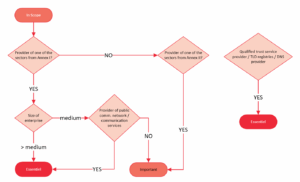
For more information, please visit our page on the scope and field of application of NIS2.
The highly critical (so-called essential) sectors are those identified in Annex I of the NIS2 Directive, namely:
For more information, please visit our page on NIS 2.
The other critical (i.e. important) sectors are those identified in Annex II of the NIS2 Directive, namely:
For more information, please visit our page on SERIMA.
Unlike the situation under the NIS 1 Directive, competent authorities no longer need to designate entities falling within the scope of the NIS 2 Directive. Entities will have to analyse their situations individually and, where necessary, comply with the obligations arising from the NIS 2 Directive.
Furthermore, the NIS 2 Directive requires the ILR to draw up a list of essential and important entities, as well as entities providing domain name registration services, by 17 April 2025 at the latest. In order for the ILR to achieve this objective, and in accordance with Article 3(4) of the NIS 2 Directive, entities falling within the scope of the NIS 2 Directive are obliged to submit all the information requested via the self-registration form available on the ILR website.
Upon receipt of the self-registration form, the ILR will review and confirm the status of the entity in question (i.e. status as an essential or important entity). The ILR may request additional information from the entity in question to process or complete the file. Furthermore, entities are required to notify the ILR of any changes to the information they have previously provided within two weeks of the date of the change.
Nevertheless, the ILR can still identify an entity as important or essential due to its criticality for Luxembourg, even if it does not fall within the scope of NIS2 by default.
By 17 April 2025 at the latest, the competent authority must notify the European Commission and the Cooperation Group of the number of entities for each sector and subsector.
Article 3 of draft law no. 8364, which aims to transpose the NIS 2 directive into national law in the Grand Duchy of Luxembourg, assigns to the ILR the function of competent authority for the security of networks and information systems for the vast majority of sectors. Furthermore, the same article entrusts the Commission de Surveillance du Secteur Financier (CSSF) with the role of competent authority for the banking sector and the financial market infrastructure sector, as well as for the digital infrastructure sector and the ICT service management sector, regarding the activities that fall under the supervision of the Commission de Surveillance du Secteur Financier.
This date will depend on the entry into force of the future law transposing the NIS 2 Directive into Luxembourg law. The NIS 2 Directive provides for an obligation for competent authorities to transmit data related to the number of essential and important entities to the European Commission by 17 April 2025 at the latest.
Entities already covered by the NIS1 Directive will automatically be classified as essential entities under NIS2.
However, self-registration is still recommended to enable the collection of additional information needed to comply with the new Directive.
An operator covered by the Telecom Law, already subject to security measures obligations, will be registered as an essential entity under NIS2, unless it self-registers. In this case, its situation will be assessed according to the classification scheme provided for, and it may be reclassified as an important entity if the conditions are met.
In any case, self-registration is still recommended in order to allow the collection of additional information necessary for compliance with the new directive.
The obligations concerning major/significant incidents are derived from Article 23 of the NIS 2 Directive. An incident is considered major/significant if:
“(a) it has caused or is capable of causing severe operational disruption of the services or financial loss for the entity concerned;
(b) it has affected or is capable of affecting other natural or legal persons by causing considerable material or non-material damage.”
After the transposition of the NIS 2 Directive into Luxembourg law, the ILR will publish more precise criteria and indicators on this subject by means of a regulation.
As defined in paragraph 11 of Article 23, the Commission will adopt implementing acts specifying in more detail the cases in which an incident is to be considered important for DNS service providers, top-level domain name registries, cloud service providers, data centre service providers, content delivery network providers, managed service providers, managed security service providers, as well as providers of online marketplaces, online search engines and social networking platforms.
Article 6(6) of the NIS 2 Directive defines an incident as ‘an event compromising the availability, authenticity, integrity or confidentiality of stored, transmitted or processed data or of the services offered by, or accessible via, network and information systems’.
If an incident with a significant impact occurs, whether due to an act of malice or improper handling, it must be reported in all cases.
Any event, including natural threats, that compromises the availability, authenticity, integrity or confidentiality of stored or transmitted data or data that is being processed, or of the services offered by or made accessible through networks and information systems, falls within the scope of the NIS 2 Directive. Incidents outside this scope do not need to be reported to the ILR.
For example, a truck hitting an electricity circuit distributor does not fall within the scope of the NIS2 directive, even if this incident impacts the operational activities of the electricity supply service. However, a truck hitting an electronic communications distributor does fall within the scope of NIS2, given that there is an impact on network equipment and information systems.
It is important that entities identify all types of threats as part of the risk management process to plan and implement adequate security measures, e.g. a physical security perimeter, redundancy of critical systems, etc.
According to Article 23, paragraph 4, subparagraph a of the NIS 2 Directive, entities are obliged to submit to the CSIRT (Computer Security Incident Response Team) or, as the case may be, to the competent authority “ without undue delay and in any event within 24 hours of becoming aware of the significant incident, an early warning, which, where applicable, shall indicate whether the significant incident is suspected of being caused by unlawful or malicious acts or could have a cross-border impact”.
Here, it is important to distinguish between the time of the occurrence of a significant incident and the time of its detection. Indeed, there may be a delay of only a few minutes between occurrence and detection, or even a few years, if we consider cyber threats that have advanced and complex capabilities and that are state sponsored.
In conclusion, an entity is obliged to report a significant incident within 24 hours of detecting it, even outside working hours.
Currently, operators of essential services and digital service providers report their incidents to the ILR using the form provided for this purpose on the ILR website.
In the near future, for the implementation of the NIS 2 directive, an ‘incident reporting’ module is expected to be integrated into the SERIMA tool so that entities can report significant incidents.
For more information, please visit our page on SERIMA.
The ILR collaborates with the various players in the cybersecurity ecosystem with the aim, among other things, of simplifying the procedures relating to incident notification.
For the time being, draft law no. 8364 transposing the NIS 2 directive into national law stipulates that essential and important entities must notify all incidents to the competent authority within 24 hours of their detection. The competent authority then forwards the notification to the relevant CSIRT (Computer Security Incident Response Team) and to the single point of contact.
However, this obligation does not prevent the entity from transmitting information relating to the incident to its own CSIRT.
The ILR will inform the entities about the incident notification procedure.
By taking a collaborative approach, the ILR is doing every effort to find synergies with the other authorities concerned in order to have uniform criteria and means and thus contribute to the effectiveness of each entity’s activities.
In this context, an ‘incident reporting’ module is to be integrated into the SERIMA tool as a national incident notification platform, in a way that entities can notify incidents to other authorities. This will simplify the entities’ notification procedures.
In principle, important entities must adopt the same security requirements specified in the NIS 2 directive as essential entities. The main difference between these two categories of entities lies in the level of supervision by the competent authority.
Essential entities will be subject to a regime of ex ante, and ex post supervision, which corresponds to ‘complete’ supervision. Important entities will only be subject to an ex post supervision regime. Important entities will therefore be exempted from the regular provision of certain deliverables (e.g. risk analysis, description of security measures in place) that essential entities will have to provide. In the event of an incident, it may also be necessary for important entities to provide additional information on the security measures implemented at the request of the ILR.
| Mechanism | To be sent to ILR | Essential entity | Important entity |
|---|---|---|---|
| Ex-ante | Security measures | ✓ | ✗ |
| Ex-post | Incident notification | ✓ | ✓ |
| Ex-post | After incident & upon request | ✓ | ✓ |
Article 21(1) of the NIS 2 Directive stipulates that entities will be obliged to take all necessary, appropriate and proportionate technical, organisational and operational measures to manage the risks threatening the security of their networks and information systems or used in the context of their activities or in the provision of their services.
Furthermore, Article 21(2)(h) and (j) of the NIS 2 Directive requires entities to apply measures based on an ‘all-hazards’ approach in the areas of encryption and multi-factor authentication:
“2. The measures referred to in paragraph 1 shall be based on an all-hazards approach that aims to protect network and information systems and the physical environment of those systems from incidents, and shall include at least the following:
…
h) policies and procedures for the use of cryptography and, where appropriate, encryption;
…
j) the use of multi-factor authentication or continuous authentication solutions, secured voice, video and text communications, and secure emergency communication systems within the entity, where appropriate.’
Although these two measures are technical in nature, the objective of policies and procedures, which are organisational measures, is to align the technical aspects with the strategic aspects of the entity.
While the NIS 2 Directive does not define the criteria for the implementation of encryption and MFA measures, the ILR recommends that entities follow best practices in accordance with European and international standards.
The ILR is currently working on defining the security measures to be implemented by entities under the NIS 2 Directive.
For more information, please visit our page on SERIMA.
Currently, operators falling within the scope of the NIS 1 law, as well as those falling within the scope of Articles 42, paragraph 1 and 43, paragraph 2 of the law of 17 December 2021 on electronic communications networks and services, are obliged to notify the ILR of the security measures they have put in place. This notification is done, among other things, by sending a form on the measures in place based on security objectives proposed by ENISA. This file can be downloaded and viewed here.
The ILR is currently working on the security measures to be implemented in accordance with the NIS 2 directive as well as the good practices to be followed. The security measures will in principle be aligned with European and international standards (e.g. ISO/IEC 2700x) and existing good practices (e.g. CyberFundamentals by CCB).
For more information, please visit our page on SERIMA.
The assets currently configured in SERIMA will be reviewed and adapted as required under the NIS 2 Directive. The ILR will inform the entities regarding the asset adaptations.
For more information, please visit our page on SERIMA.
Discover links to related pages to deepen your knowledge and explore similar topics.
The NISS department ensures that the law regarding the security of networks and information systems is properly enforced in several sectors.